
Global Software Designed Perimeter Market Size, Trends, and Analysis - Forecasts To 2026 By Component (Solutions [Access Control, Risk Analytics and Visualization, Security Compliance and Policy Management, Performance Management and Reporting, Others {Control Automation and Orchestration, Data Loss Prevention (DLP), Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)}], Services (Consulting and Implementation,[Training, Support, and Maintenance]), By Connectivity (Controller, Gateway, End Point), By Deployment Mode (Cloud, On-Premises), By Organization Size (Small and Medium-sized Enterprises, Large Enterprises),By Region (North America, Asia Pacific, CSA, Europe, and the Middle East and Africa); End-User Landscape, Company Market Share Analysis & Competitor Analysis
Software-designed perimeter is a cybersecurity system created to micro-segment the access to the network based on the user access. The security was created to prevent common network attacks like pass-the-ticket, pass-the-hash, service scanning, SQL injections, and other common exploits used by hackers to access confidential data. In recent years, the number of cyberattacks has been on the rise which has increased the demand for cybersecurity systems to protect networks. The software-designed perimeter system revolves around providing access based on the user’s identity rather than the IP address of the device. All the endpoints requesting access are provided access based on authorization to said data and are authenticated before access is provided. By restricting access to users, the area of attack will be lowered considerably improving the system’s security. With recent advancements in cloud technology, companies are investing in cloud-based IT services like IoT to increase efficiency. This has increased the threat of access by unauthorized users accessing confidential data even allowing them to take control of the entire network. With the help of software-designed perimeter systems, such threats can be neutralized to a large extent. The COVID-19 pandemic has increased the number of employees working from their homes which has increased the number of users accessing information from IP addresses outside the network. Before the pandemic, the number of employees working from home was as low as 16% but after the restrictions, this number has increased to over 65% and a large number of companies expect this system of work to continue past the pandemic. Combined with the growing trend of BYOB (bring your device), the market for software-designed perimeter systems has thrived and is expected to register a large growth during the forecast period. Software-designed perimeter systems are cheaper and more efficient to implement than other security systems like sophisticated firewalls, multi-factor authentication, and virtual point-to-point (VPN) systems. The market for software-designed perimeter is restricted by a lack of awareness among employees about network breaches, the need for a skilled labor force to implement such systems, and the need for stringent policies to implement software-designed perimeter systems.
Based on the component the software-designed perimeter market is segmented into services and solutions. The solution segment includes security compliance and policy management, access control, risk analytics & visualizations, performance management & reporting, among others. The services segment includes consultation and implementation, training, support, and maintenance. The solutions segment had the majority of the shares in the market as companies are increasingly outsourcing cybersecurity instead of having an in-house cybersecurity department.
According to the mode of connectivity, the software-designed perimeter market can be segmented as endpoint, gateway, and controller. The endpoint segment had the majority of the shares in the market. The endpoint management is a vital part of the software-designed perimeter security system. The endpoint refers to the device that is attempting to connect to the network and only through authentication of the device can they be given access. The endpoint is verified through the gateway and then given controlled access, the endpoint security plays a vital part and there is an increasing demand for efficient, easy to use, and secure endpoint management systems in the security framework.
Based on the deployment mode, the software-designed perimeter market can be segmented into cloud and on-premise. The cloud segment had the majority of the shares in the market and also will be the fastest-growing segment from 2021 to 2026. The rising implementation of cloud systems by companies is a major driver of the demand for this segment. Cloud systems make it possible for employees to access relevant information from remote areas securely, interconnectivity between offices, and multiple user access. These systems have increased in demand due to the rise in the number of WFH and BYOD work trends.
Based on the size of the organization, the software-designed perimeter market can be segmented as small and medium enterprises and large enterprises. The small and medium enterprises segment had the majority of the shares in the market. Small and medium enterprises are turning to software-designed perimeter security systems to protect their networks as it is cheaper. Small and medium enterprises do not have the same financial capability as large enterprises making it cheaper for them to outsource their cyber-security needs. With the growing implementation of cloud-based solutions, small and medium enterprises are encouraging employees to work from home and use their own devices as a way to cut costs. This increases the need for software-designed perimeter systems among small and medium enterprises.
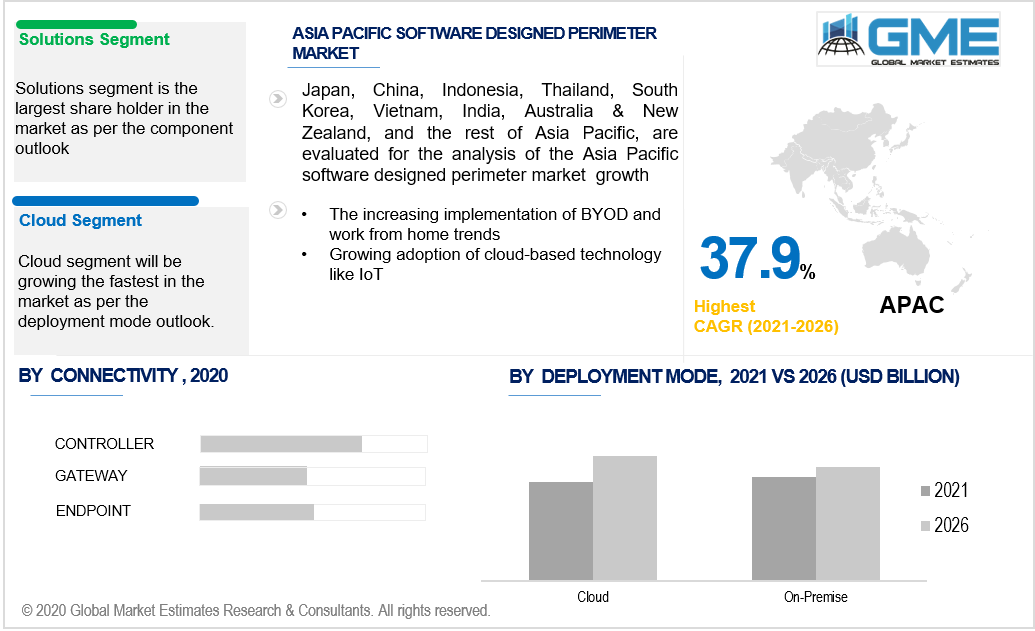
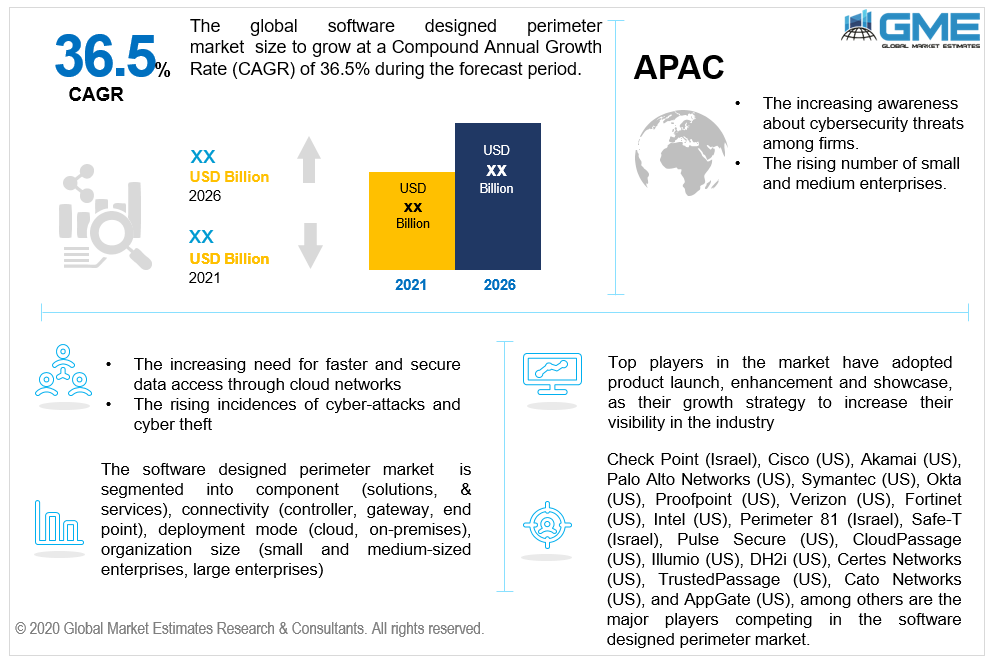
The North American region segment had the majority of the shares in the market. The North American region houses a large number of enterprises that are global leaders and are more susceptible to cyberattacks than a smaller firm. The rising incidences of cyber-attacks in the region and growing privacy concerns are the major drivers for the software-designed perimeter market in the region. The growing adoption of cloud-based technologies like IoT in the region has all contributed to the need for sophisticated security systems. The region has been quick to implement WFH and BYOD even before the pandemic situation which has had a positive impact on the market in the region. The APAC region will be dominant in terms of CAGR value. The rising number of small and medium enterprises in the region has increased the demand for software-designed perimeter systems in the region. The growing concern about privacy and the need to protect themselves from cyberattacks among firms have had a positive impact on the software-designed perimeter market. There is a rising number of software-designed perimeter vendors in the region as the number of skilled labor available in the region increases.
Cisco (US), Check Point (Israel), Akamai (US), Symantec (US), Palo Alto Networks (US), Okta (US), Verizon (US), Proofpoint (US), Fortinet (US), Perimeter 81 (Israel), Intel (US), Safe-T (Israel), CloudPassage (US), Pulse Secure (US), Illumio (US), Certes Networks (US), DH2i (US), TrustedPassage (US), AppGate (US), and Cato Networks (US), among others, are the major vendors competing in the software designed perimeter market.
Please note: This is not an exhaustive list of companies profiled in the report.
We value your investment and offer free customization with every report to fulfil your exact research needs.
The Global Software Designed Perimeter Market has been studied from the year 2019 till 2026. However, the CAGR provided in the report is from the year 2021 to 2026. The research methodology involved three stages: Desk research, Primary research, and Analysis & Output from the entire research process.

The desk research involved a robust background study which meant referring to paid and unpaid databases to understand the market dynamics; mapping contracts from press releases; identifying the key players in the market, studying their product portfolio, competition level, annual reports/SEC filings & investor presentations; and learning the demand and supply-side analysis for the Software Designed Perimeter Market.
The primary research activity included telephonic conversations with more than 50 tier 1 industry consultants, distributors, and end-use product manufacturers.
Finally, based on the above thorough research process, an in-depth analysis was carried out considering the following aspects: market attractiveness, current & future market trends, market share analysis, SWOT analysis of the company and customer analytics.

Tailor made solutions just for you
80% of our clients seek made-to-order reports. How do you want us to tailor yours?
OUR CLIENTS